Limitations of Access Control Lists in Network Security
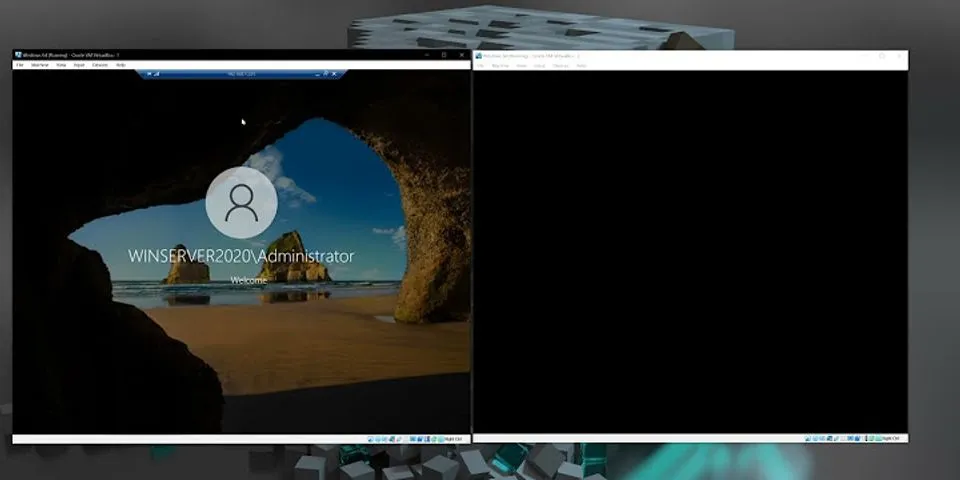
Reference this Show Share this: Facebook Facebook logo Twitter Twitter logo Reddit Reddit logo LinkedIn LinkedIn logo WhatsApp WhatsApp logo Access control list limitationsWhen the application server is running multiple applications on the same IP address, same port and of the same protocol, the access control list (ACL) rules might not be applied reliably and there is a vulnerability. For example, app1 and app2 are hosted on the same server, app.example.com. An ACL rule is set up to allow User A access to app1.app.example.com. If an attacker modifies the application parameters, such as the host header, before it reaches the EAA Client, then the EAA Client will not be able to detect it. This allows the attacker to access app2.app.example.com maliciously. Note: The EAA Client does not perform termination, decryption, or deep-inspection of the application payload for tunnel-type client-access applications. Advantage:Prevention of TheftAn access control system's primary task is to restrict access. This is critical when access to a person's account information is sufficient to steal or alter the owner's identity. Many websites that require personal information for their services, especially those that need a person's credit card information or a Social Security number, are tasked with having some sort of access control system in place to keep this information secure. Video of the Day Types of ACLsIn general, an access control list is exactly what its name suggests: a list that governs access to a particular resource. ACLs can be used in a number of different contexts, but two of the most common are governing permissions on file systems and at the network level.
In a filesystem, an ACL is designed to help the operating system determine the levels of access that a particular user has with regard to a certain file or directory. Commonly, these permissions state whether or not a user has the ability to read, write, and/or execute a particular file. In Linux, ACLs are available as an supplement to traditional permission management, where file permissions must be set on a per-file or per-folder basis. With an ACL, an administrator can assign certain permissions or sets of permissions to a given user very easily. This enables a certain user or group to be given certain permissions for a file by the file owner even if that owner does not have the power to manage the given group.
ACLs can also be applied at the network level, where they can be used in a variety of ways. Network ACLs can provide performance improvements by implementing restrictions on certain types of traffic or for a particular region of the network. They also provide security benefits since they can restrict communications between different systems or over certain protocols as needed. At the network level, two main types of ACLs exist. A standard ACL applies restrictions based solely upon the source IP address of traffic. For example, a protection against data exfiltration may be blocking any traffic coming from the main database server from crossing the organization’s network perimeter. Since the database server should not be communicating with external systems directly, this could help to detect and block potentially malicious traffic. However, this standard ACL could not differentiate different types of traffic and make decisions accordingly. An extended ACL uses the source and destination addresses and ports in its analysis. This enables a network administrator to define much more granular rules regarding the types of traffic that are permitted to pass through and the types that should be blocked. This is helpful if, for example, an administrator wishes to decrease the attack surface of a web server by limiting traffic to and from it to only traffic flowing on legitimate HTTP(S) ports (80 and 443). Access Control Definitions and LimitationsThe esadm group can specify ACL features for users and groups for the following components:
|